The Tor Network is known for being synonymous with the DarkWeb. The “Tor” in Tor Network stands for “The Onion Router”. There is good reason for that without the Tor Network there would be no DarkWeb. The Tor Network was made by the United States Naval Research Laboratory in the mid 1990’s. The aim of the project was to protect communications between intelligence assets in different countries. It was released to the public 2002 and is maintained by a Non-Profit organization.
How does the Tor Network Work
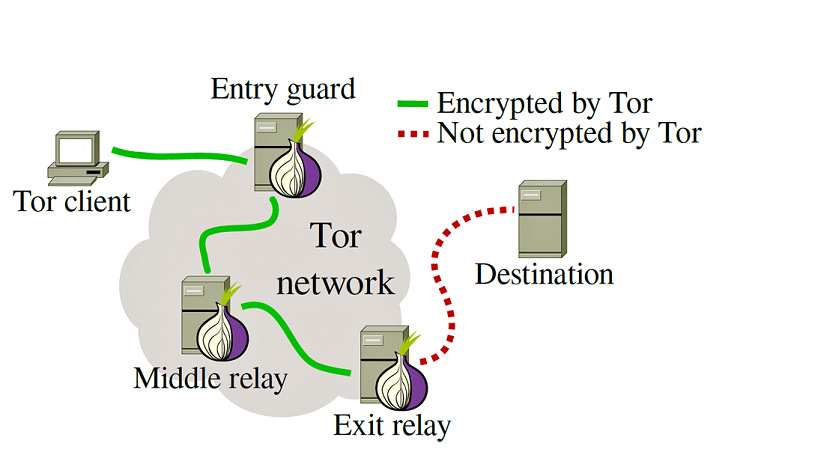
The Tor Network operates by routing traffic through many different nodes, or relays that are run by volunteers around the country and around the world. The nodes operate in a way where they only know the node they received the message from and they know the node they send the message too. Theses nodes cannot access any other information about the destination of the information it received and sent concealing the identity the user and the message.
Here is a Step by Step breakdown of how the Tor network operates
- When a user wants to access the internet anonymously through Tor, they first need to download and install the Tor browser from their website or download an app on their mobile device.
- When you launch the Tor browser, it connects to a random entry node in the network. The entry node is the first rely chain and is responsible for encrypting the user’s internet traffic before sending it on to the next node in the chain.
- Then your traffic is then routed through a series of middle relays, these middle relays further encrypt the data and obscure your online activity. As said before each relay only knows the next relay it sends information to and the previous relay also.
- Finally, your internet traffic reaches an exit node, which decrypts all your data and sends it to its final destination which could be a website. The exit node is the last node in the chain and is the only one that knows your final destination.
- The website or server that you are accessing receives the information from the exit node, they have no way of knowing where the original request came from, thus not revealing your identity, IP address or your location. This process makes it very difficult to track any users internet traffic on the Tor.
It is very important to note that while the Tor Network provides a high level of anonymity and privacy, there is still room for it to fail. You still need to take precautions from clicking on certain links or downloading files in this part of the web. There are attacks that people can still use when you are operating on the Tor Network, these attacks can be exit node eaves dropping and website fingerprinting.
Here is a visualization of the process
Onion addresses
The website names on Tor, also known as “onion” addresses, work through a special addressing system that allows websites to be accessed anonymously and securely over the Tor network
Onion Addresses are made up of a series of 16 random characters followed by “.onion”. The characters are generated using a public key of the website’s server, and are unique to each onion address. When you enter an onion address into a Tor browser, the Tor network established encrypted connection to the server hosting the website.
Regular Domains are usually are usually registered with a centralized authority like ICANN. Onion address are not registered with a centralized authority they are generated by the websites server using an algorithm called SHA-1. There can be no censorship with these domains because they are not centralized and since there are not registered its very hard to know who owns the domain.
Its important to note that onion addresses are only accessible through the Tor Network.
Notable Websites
The Hidden Wiki
A popular directory for all sorts of Tor websites without having to memorize all the special onion addresses
ProPublica
A nonprofit investigative journalism organization that operates a Tor hidden service to allow anonymous sources to securely submit tips and documents.DuckDuckGo: A privacy-focused search engine that operates a Tor hidden service, allowing users to search the web anonymously
Learn about where your data goes after its stolen