Middle Man or Man in the Middle (MitM) cyber attacks are cheap and relativley easy hacks to deploy in public areas that not many people know how to protect against. This attack can result in Eavesdropping on your communication which can gain access to private information like passwords or credit card numbers. Data manipulation which the attacker can alter the messages or information sent between two parties. Credential theft, which means the attacker is intercepting your login in credentials for whatever site you are currently trying to log into or are logged into. The most significant injury they can cause is Malware Infection which means they can gain control of your computer even when you are not actively being harmed through the Man in the Middle attack.
What is Man in the Middle (MiTM) cyber attack?
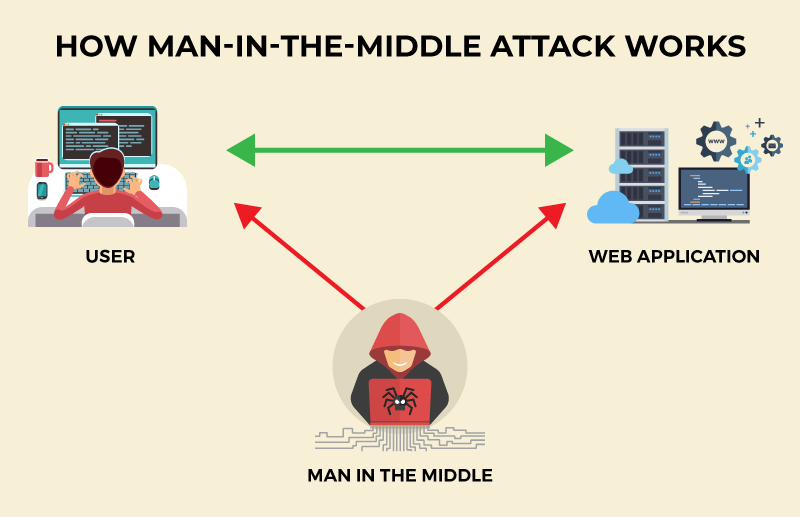
A Man in the Middle (MitM) attack is a cyber attack where an attacker intercepts and can alter communication between two parties who believe they are communicating securely with each other.
- First the attacker has to position themselves between the two victims who are communicating. This can be done by physically putting themselves into the network, or by exploiting a vulnerability in the network or one of the parties to gain access to the communication stream.
- Once they are in the correct position, they intercept the communication stream between the devices or parties communicating. This can be done by relocating the communication path way where it is intercepted or just eaves dropping. .
- Next their is a choice by the attacker to either passively look at the communication or actively alter the communication between the parties. In a passive attack, the attacker simply eaves drops on the communication stream and collects any or all sensitive information between the parties. To actively alter communication, they can change the information being sent between the two parties such as direct change of messages sent or even redirecting where the information is sent.
- In some instances, the attacker may impersonate one of the parties to gain specific information they may be looking for rather than waiting for that information to come naturally from the parties. \
It can be executed using varying techniques, like DNS spoofing, WiFI eavesdropping and session hijacking. The main ways to prevent against these attack its important to always use secure communication protocols like HTTPS or SSL/TLS and regularly updating your browser and OS software.
Most Common Locations for Man in the Middle (MitM) Cyber Attacks
Coffee shops, libraries and other types of public areas are the most common places for people to be very productive when completing work, these places set up WiFi connections knowing this to attract more people. This can be a great thing but when these connections are setup it is not done with security in mind. It is usually done with the intent to have many people access a good connection without any issues. This leads to a great target for attackers.
Public WiFi networks: These networks allow anyone to access them leaving them unsecure.
Corporate Networks: Attackers can use MitM attacks to intercept and steal sensitive information such as login credentials, financial data, or intellectual property.
Online banking and e-commerce sites: Attackers can intercept the communication stream between the user and the site, potentially gaining access to sensitive data such as credit card numbers or bank account information.
Email and messaging apps: MitM attacks can also be used to intercept and read messages sent through email and messaging apps.
Mobile devices: MitM attacks can occur on mobile devices, particularly if the device is connected to an unsecured Wi-Fi network.
Best techniques to avoid Man in the Middle (MitM) Cyber Attack
Use Secure communication protocols: HTTPS, SSL/TLS, or VPN, encrypt the communication stream and make it more difficult for attackers to intercept and change
Avoid unsecured public Wi-Fi networks the data: As mentioned before Public Wi-Fi networks are often unsecured and can be a prime target for MitM attacks. f you must connect to one, use a VPN to encrypt the communication stream and prevent attackers from intercepting and modifying the data.
Keep software up to date: Attackers often exploit vulnerabilities in software to carry out MitM attacks. Older pecies of software always have known ways to be exploited.
Verify the identity of the recipient: MitM attacks can involve impersonating one of the parties involved in the communication. To stop this from happening it is important to employ two-factor authentication.
Be cautious of suspicious links and attachments: MitM attacks can be carried out through phishing emails or other types of social engineering attacks. Never click on a link unless it is expected from a verified source.
1 thought on “Middle Man Cyber Attack, It’s More Common Than You Think”
Comments are closed.