Encryption, Do you need it?
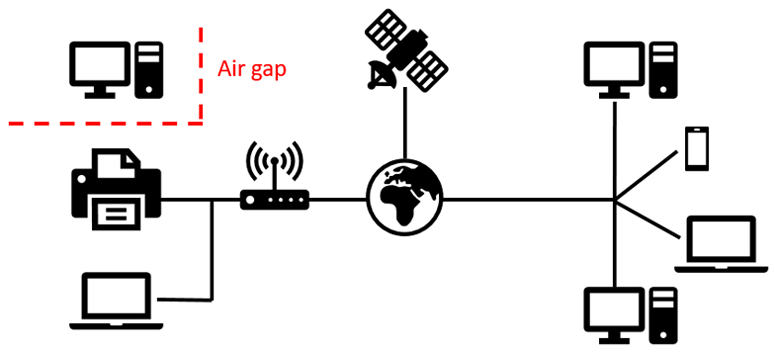
Encryption is a key component of online security and keeping all your data safe from online hackers and bad actors. What is Encryption? Encryption is the process of encoding information. This process converts the plain text of code into an alternative form known ciphertext. Ideally only an authorized party can decipher the ciphertext back to …