How to Find and Delete Metadata
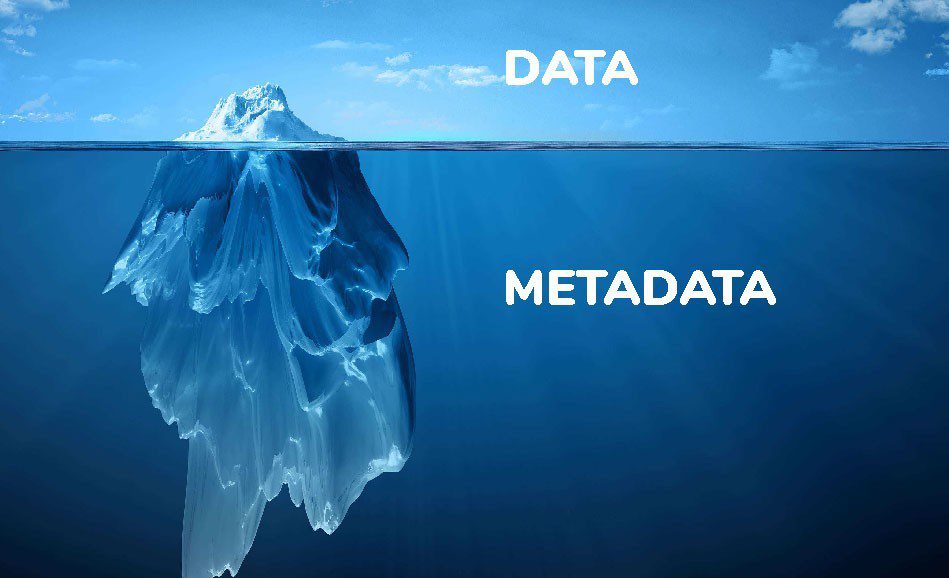
Metadata can be located in any kind of document of piece of data that is created by a user. Just as easy as it can be created, metadata can be deleted and removed. First we must explain what metadata is. What is Metadata? We’ve already discussed this in a previous post, called “How to Remove …